Let’s Encrypt is a Certificate Authority (CA) that facilitates obtaining and installing free TLS/SSL certificates, thereby enabling encrypted HTTPS on web servers. It streamlines the process by providing a software client, Certbot, that attempts to automate most (if not all) of the required steps. Currently, the entire process of obtaining and installing a certificate is fully automated on both Apache and Nginx.
In this guide, you’ll use Certbot to obtain a free SSL certificate for Apache on Raspberry Pi and make sure this certificate is set up to renew automatically.
This tutorial uses a separate virtual host file instead of Apache’s default configuration file for setting up the website that will be secured by Let’s Encrypt. We recommend creating new Apache virtual host files for each domain hosted in a server because it helps to avoid common mistakes and maintains the default configuration files as a fallback setup.
Step 1 — Installing Certbot
To obtain an SSL certificate with Let’s Encrypt, you need to install the Certbot software on your server. You’ll use the default Ubuntu package repositories for that.
First, update the local package index:
sudo apt updateYou need two packages: certbot, and python3-certbot-apache. The latter is a plugin that integrates Certbot with Apache, making it possible to automate obtaining a certificate and configuring HTTPS within your web server with a single command:
sudo apt install certbot python3-certbot-apacheYou will be prompted to confirm the installation by pressing Y, then ENTER.
Certbot is now installed on your server. In the next step, you’ll verify Apache’s configuration to make sure your virtual host is set appropriately. This will ensure that the certbot client script will be able to detect your domains and reconfigure your web server to use your newly generated SSL certificate automatically.
Step 2 — Checking your Apache Virtual Host Configuration
To automatically obtain and configure SSL for your web server, Certbot needs to find the correct virtual host within your Apache configuration files. Your server domain name(s) will be retrieved from the ServerName and ServerAlias directives defined within your VirtualHost configuration block.
If you followed the virtual host setup step in How to Setup a Raspberry Pi Apache Web Server, you should have a VirtualHost block set up for your domain at /etc/apache2/sites-available/your_domain.conf with the ServerName and also the ServerAlias directives already set appropriately.
To confirm this is set up, open the virtual host file for your domain using nano or your preferred text editor:
sudo nano /etc/apache2/sites-available/your_domain.confFind the existing ServerName and ServerAlias lines. They should be listed as follows:
/etc/apache2/sites-available/your_domain.conf
...
ServerName your_domain
ServerAlias www.your_domain
...
If you already have your ServerName and ServerAlias set up like this, you can exit your text editor and move on to the next step. If your current virtual host configuration doesn’t match the example, update it accordingly. If you’re using nano, you can exit by pressing CTRL+X, then Y and ENTER to confirm your changes, if any. Then, run the following command to validate your changes:
sudo apache2ctl configtestYou should receive Syntax OK as a response. If you get an error, reopen the virtual host file and check for any typos or missing characters. Once your configuration file’s syntax is correct, reload Apache so that the changes take effect:
sudo systemctl reload apache2With these changes, Certbot will be able to find the correct VirtualHost block and update it.
Next, you’ll update the firewall to allow HTTPS traffic.
Step 3 — Allowing HTTPS Through the Firewall
To allow the Apache Full profile through the firewall on a Raspberry Pi web server using ufw, you can follow these steps:
- Enable
ufw: Ifufwis not already enabled, enable it by running the following command:
sudo ufw enable- Allow Apache Full profile:
ufwcomes with predefined application profiles, and the “Apache Full” profile allows both HTTP (port 80) and HTTPS (port 443) traffic. Run the following command to allow the Apache Full profile:
sudo ufw allow 'Apache Full'This command enables incoming traffic on ports 80 and 443 for both HTTP and HTTPS.
- Verify the rules: You can check the status of
ufwand verify that the Apache Full profile rule is correctly configured by running the following command:
sudo ufw statusEnsure that the rules allowing ports 80 and 443 are listed in the output, associated with the “Apache Full” profile.
- Test the HTTP and HTTPS connections: Verify that both HTTP and HTTPS traffic is allowed by accessing your website over both protocols (e.g., http://yourdomain.com and https://yourdomain.com) from a client machine. If the connections are successful, it means the firewall is allowing the Apache Full profile.
Please note that by allowing the Apache Full profile, you’re opening up ports 80 and 443 to incoming traffic, which includes both HTTP and HTTPS. It’s important to ensure that your Apache server is properly configured to handle HTTPS traffic with valid SSL certificates. Additionally, consider implementing other security measures like rate limiting, filtering by source IP, or enabling a Web Application Firewall (WAF) to enhance security for your web server.
Step 4 — Obtaining an SSL Certificate
To obtain an SSL certificate for your Raspberry Pi web server, you can use Certbot, a popular tool that automates the process of obtaining and installing SSL certificates from Let’s Encrypt. Here’s how you can do it:
- Install Certbot: Begin by installing Certbot on your Raspberry Pi by running the following commands:
sudo apt updatesudo apt install certbot
- Choose the Certbot plugin: Certbot supports various plugins for different web servers. Since you’re using Apache on your Raspberry Pi, you can use the Certbot Apache plugin. Install the plugin by running the following command:
sudo apt install python3-certbot-apache
- Obtain the SSL certificate: Run Certbot with the Apache plugin to automatically obtain and install the SSL certificate for your domain. Execute the following command:
sudo certbot --apache
- Certbot will guide you through the process, prompting you to select the domain you want to secure and providing options to configure your SSL settings.
- Configure HTTPS settings: Certbot will automatically configure Apache with the SSL certificate. However, depending on your specific requirements, you may need to make additional adjustments to your Apache configuration. For example, you might want to redirect all HTTP traffic to HTTPS or enable specific SSL protocols and ciphers. Modify your Apache configuration files accordingly.
- Test SSL configuration: Restart Apache to apply the changes and test your SSL configuration. Make sure your website loads correctly over HTTPS without any certificate warnings or errors. You can use online SSL testing tools like SSL Labs (https://www.ssllabs.com/ssltest/) to check the security and validity of your SSL certificate.
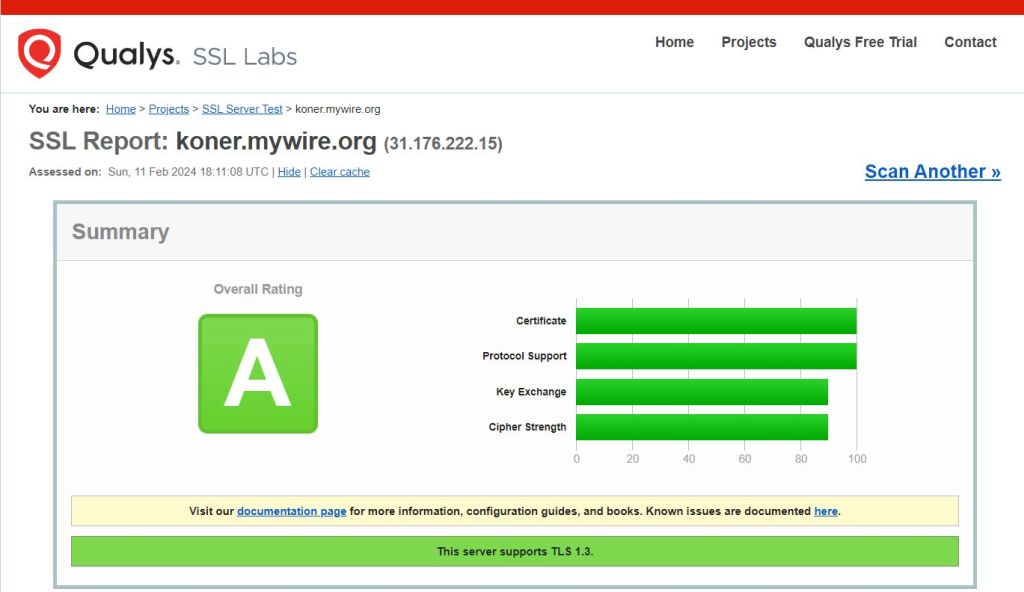
By following these steps, you can obtain and install an SSL certificate for your Raspberry Pi web server using Certbot. Remember to regularly monitor and renew your SSL certificate to maintain a secure configuration.
Step 5 — Verifying Certbot Auto-Renewal
Let’s Encrypt’s certificates are only valid for ninety days. This is to encourage users to automate their certificate renewal process, as well as to ensure that misused certificates or stolen keys will expire sooner rather than later.
The certbot package you installed takes care of renewals by including a renew script to /etc/cron.d, which is managed by a systemctl service called certbot.timer. This script runs twice a day and will automatically renew any certificate that’s within thirty days of expiration.
To check the status of this service and make sure it’s active, run the following:
sudo systemctl status certbot.timer
To test the renewal process, you can do a dry run with certbot:
sudo certbot renew –dry-run
Certbot keeps track of its renewal attempts and logs them in the system. You can review the logs to verify the renewal status. The log location may vary depending on your Linux distribution, but some common locations are:
/var/log/letsencrypt/letsencrypt.log/var/log/letsencrypt/renew.log/var/log/syslog
Open the appropriate log file using a text editor and search for renewal-related entries. Look for successful renewal messages or any error messages that might indicate a problem with the renewal process.
If you don’t receive any errors, you’re all set. When necessary, Certbot will renew your certificates and reload Apache to pick up the changes. If the automated renewal process ever fails, Let’s Encrypt will send a message to the email you specified, warning you when your certificate is about to expire.